Overview of the SSO flow
The following figure shows a basic SSO scenario in which a PingFederate server authenticates users to an SP application using the Workspace ONE IdP Adapter and PingFederate X.509 Certificate Adapter.
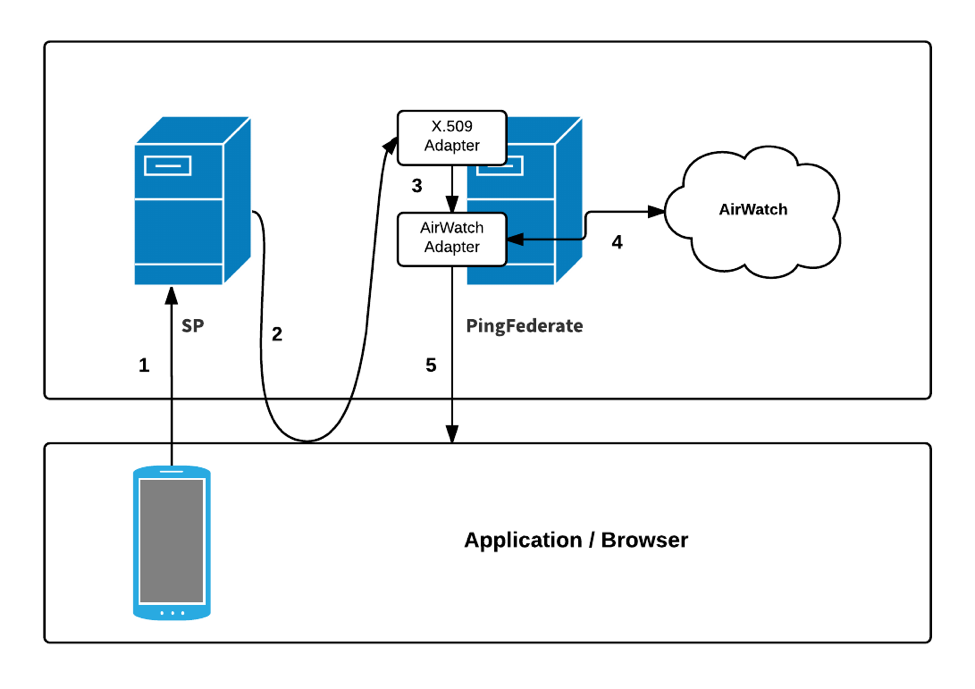
Description
-
A user with a device enrolled in Workspace ONE requests access to an SP resource. The request is redirected to PingFederate to perform X.509 authentication.
-
The browser requests the user’s X.509 certificate. The PingFederate X.509 Certificate Adapter validates the certificate against a list of issuers. If there aren’t any issuers specified in the X.509 Certificate Adapter configuration, the adapter uses the server’s list of trusted CAs instead.
-
PingFederate validates the certificate, then passes the device ID from the certificate to the Workspace ONE IdP Adapter.
-
PingFederate contacts the Workspace ONE API and provides the device ID to get information about the device’s security posture.
-
PingFederate returns the authentication result. If authentication was successful, the user is redirected to the requested resource.