Overview of the SSO flow
With the Google Login Integration Kit, PingFederate includes the Google API in the sign-on flow.
The following figure illustrates a service provider (SP)-initiated single sign-on (SSO) scenario in which PingFederate authenticates users to an SP application using the Google IdP Adapter.
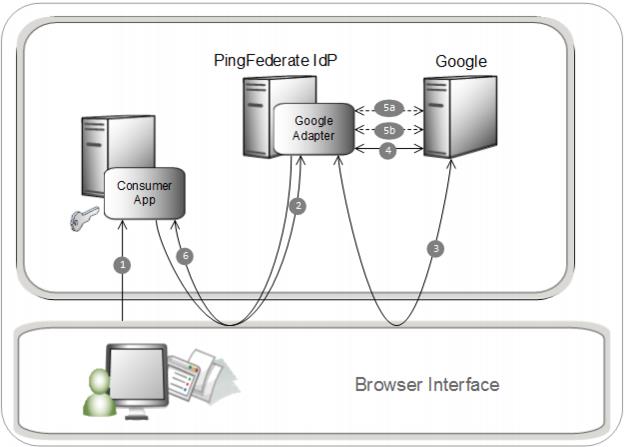
Description
-
The user opens a web application and chooses the Google Sign-In option.
-
The sign-on link points to the Google IdP Adapter, which redirects the browser…
-
…to Google for authentication with a list of requested permissions.
The user authenticates their identity and then authorizes the requested permissions. Google redirects the browser to the PingFederate Google IdP Adapter authorization callback endpoint with an authorization code.
If the user fails to authenticate or does not authorize the request, the response includes an error code instead.
-
The Google IdP Adapter makes an HTTP request to the Google API to obtain an OAuth 2.0 access token. It provides the client ID and secret, and the authorization code. The Google API returns an access token and ID token that includes the user’s email address.
-
(a) The Google IdP Adapter provides the access token and requests the email address or "Basic Profile" user attributes from the Google user info endpoint. Google returns a set of attributes in OpenID Connect format.
(b) The Google IdP Adapter provides uses a refresh token to get a new access token. It provides the access token and requests the "Extended Profile" user attributes from the Directory API (part of the G Suite Admin SDK). Google returns a set of attributes in JSON format.
-
PingFederate redirects the user to the web application with the user information from Google.