Overview of the SSO flow
With the IIS Integration Kit, PingFederate handles authentication requests to an identity provider (IdP) on behalf of IIS.
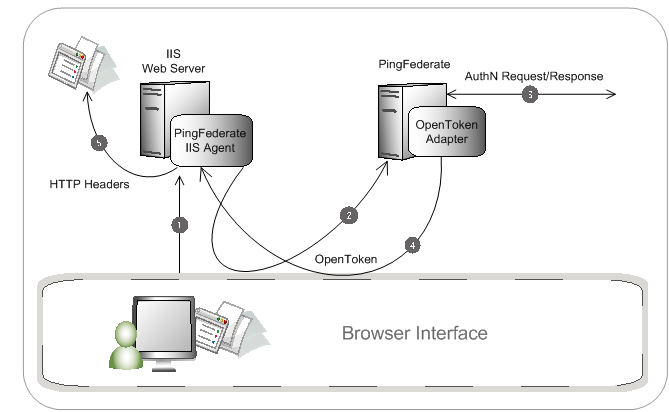
The figure above illustrates an SP-initiated SSO scenario, showing the request flow and how the PingFederate OpenToken Adapter wraps attributes from an assertion into a secure OpenToken and passes it to IIS. You can find more information in OpenToken Adapter in the PingFederate documentation.
Description
-
A user attempts to access a resource on the IIS server protected by the OpenToken IIS Agent.
-
The user is redirected to the PingFederate server for authentication.
-
If an OpenToken session already exists, the user is granted immediate access.
-
The PingFederate server redirects the user’s browser to an IdP for authentication using either the SAML or WS-Federation protocols. The IdP partner authenticates the user and returns a SAML assertion.
-
PingFederate validates the assertion and creates an OpenToken for the user including any configured attributes. PingFederate then redirects the browser, including the OpenToken, back to the OpenToken IIS Agent’s OpenToken Exchange service, which converts the OpenToken into a cookie and redirects to the original resource.
-
The OpenToken IIS Agent verifies the OpenToken and grants access to the protected resource. The User ID and any attributes from the OpenToken are exposed to the resource as HTTP Request Headers.