Overview of authentication methods
Learn about the multi-factor authentication (MFA) methods available for strong authentication.
Several authentication methods are available for strong authentication. Some are only for Workforce use cases, some are only for Customer use cases, and some can be used for both use cases.
Authentication methods are enabled and configured in the MFA policy. Learn more in Configuring an MFA policy for strong authentication.
Some authentication methods require additional configuration, and some have specific requirements and limitations. Learn more in Configuring strong authentication methods (MFA).
The following sections provide a summary of available authentication methods.
(Workforce only) PingID mobile app
Your workforce users can download an app to their mobile device and use it to sign on to your company services and applications with the added security of MFA. They can also use the app to verify their identity to an employer. The app provides several ways to authenticate and can be used when offline.
The app is fully configurable and includes a rich set of features, such as:
-
Limiting the device type, OS, and app versions that can be used
-
Preventing the use of rooted or jail-broken devices
-
Enforcing version updates
It can also be used with Mobile Device Management (MDM).
Use PingID mobile app to authenticate using:
Biometrics: Fingerprint or Facial recognition
Biometrics authentication uses a device’s native capability to scan and authenticate the user’s fingerprint or face.
-
Fingerprint authentication is supported on devices that support biometrics and are running the PingID mobile app on a supported OS.
-
Authentication by facial recognition is model-dependent for Apple and Android devices. Learn more in iPhone and iPad models that support Face ID in the Apple documentation.
Both facial recognition and fingerprint authentication results are transparently passed through to the PingID app.
You can set the biometrics authentication rollout mode with the following settings:
-
Enable and disable mobile biometrics in the PingID Mobile App MFA policy settings.
-
Define mobile biometrics settings in the PingID mobile application settings.
Configure mobile biometrics as either:
-
Preferred: If mobile biometrics are defined on the user’s device, the user must use them to authenticate. If the user doesn’t have biometrics defined on the device, they are prompted to use the Approve method.
-
Required: Users must configure mobile biometrics on a supported device and can only use biometrics to authenticate. You can optionally allow iOS users to authenticate from the lock screen or use a one-time passcode (OTP) as a fallback if biometrics are not available.
To prevent users with FaceID defined from authenticating by mistake, you can also configure PingID mobile app to explicitly request consent before each face scan is taken.
-
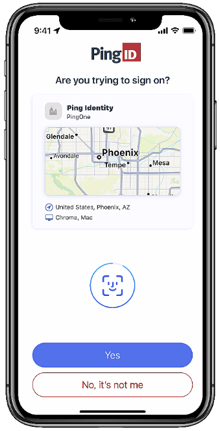
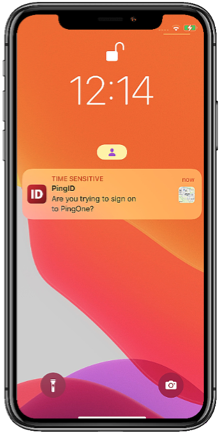
Approve a notification or Approve from Lock Screen
A push notification is sent to the user’s device to let them know they need to authenticate. If PingID mobile app is open, they can tap Yes to authenticate. If their phone is locked, or if PingID mobile app is locked, the user might be able to authenticate from the lock screen. Long-tap the notification or swipe down and tap Yes.
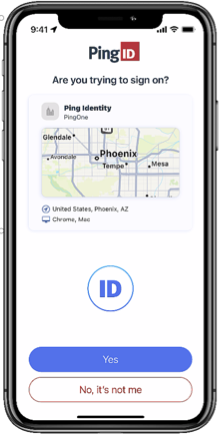
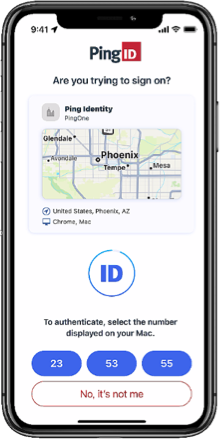
Number matching
You can require users to authenticate by selecting the number in PingID mobile app that matches the number displayed on the authenticating screen. This can be done as an additional authentication step as part of the mobile biometrics authentication or as its own authentication step. Number matching can also be performed from a user’s smart watch.
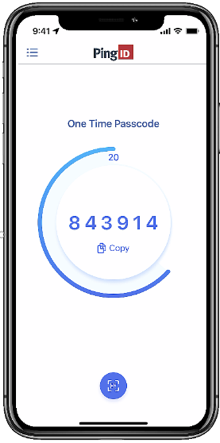
One-time passcode
PingID mobile app generates an OTP to enable users to authenticate when offline or unable to receive push notifications to your mobile device. Each OTP is unique, is valid for a limited time period, and can be used only once. When you open the PingID app, it generates a new OTP and displays a countdown timer showing when the current OTP is due to expire.
The OTP can be used for authentication in cases where the user’s mobile is offline, such as when there is no network connection, or in any other use case set by the administrator as an organization’s policy.
Smart Watch
If a user has a smart watch connected to their mobile device, the PingID mobile app automatically presents an authentication notification actions on the user’s smart watch, asking the user if they are trying to sign on, with Yes or No options. This allows the user to authenticate without needing to access their device. A smart watch can also be used for number matching authentication.
Manual Authentication (Offline authentication), and VPN access
PingID mobile app also provides the option for users to authenticate if they don’t have internet access (offline authentication) or if they want to sign on to their organization’s VPN.
(Workforce only) PingID desktop app
Your organization can enable users to download PingID desktop app to their Windows or Mac computer. They can use the app to generate an OTP with which to authenticate. Learn more in (Workforce only) Configuring the PingID desktop application.
FIDO2
PingOne MFA and PingID support the FIDO2 authentication method. FIDO2 authentication allows users to authenticate using passkeys and other FIDO2-compatible authenticators. There are a wide range of devices that can be used as a passkeys.
Biometrics are supported for the following devices:
-
Windows Hello
-
Apple Mac (Touch ID)
-
iOS biometrics (iOS 14 and later)
-
Android biometrics (Android 7 and later)
-
FIDO2 security keys
-
Non-discoverable credentials (FIDO2 devices that are not defined as passkeys) are also supported. Users can take advantage of FIDO2 strong cryptographic authentication using built-in FIDO2 platform biometrics on their device.
Authenticator app
In both Workforce and Customer environments, you can enable use of a third-party authenticator app, such as Google Authenticator or Microsoft Authenticator. An authenticator app enables your users to authenticate by generating a standard Time-based One-Time Password (TOTP). This can be useful in many scenarios, for example:
-
A workforce use case an organization cannot allow the PingID mobile app on their devices because PingID must be added to the allow list.
-
You want users to use a single authenticator app and have users that must authenticate to multiple organizations.
(Workforce only) YubiKey (Yubico OTP)
PingID workforce solutions support the use of a YubiKey with Yubico OTP capabilities as an authentication method. Select this method of authentication if you’ve distributed YubiKey hardware tokens to users who are not authenticating using a mobile device.
YubiKeys that are FIDO2 compliant can be used as either a YubiKey or a FIDO2 security key. Learn more in FIDO policies.

SMS and Voice authentication
In both Workforce and Customer environments you can enable SMS or voice authentication. PingOne sends an OTP to the user’s mobile device or landline phone using SMS or voice channels.

Learn more, including information about SMS and voice authentication and usage limits, in Configuring SMS and voice authentication.
Email authentication
You can enable email authentication in Workforce and Customer environments. PingOne sends an OTP by email to the user’s email address. Learn more in Configuring email authentication.
(Customer only) WhatsApp authentication
Enable and configure WhatsApp authentication to allow your users to receive a one-time passcode (OTP) by WhatsApp.
Learn more in (Customer Only) Configuring WhatsApp authentication
OATH token
Enable the use of OATH-compliant hard tokens to generate an OTP for secure authentication in Workforce or Customer environments.
Use hardware OATH tokens where there are no provisions for connection to the Internet, USB connections, or mobile phones. These connections could be disallowed for security reasons. Learn more in Configuring OATH token authentication.

Backup authentication
If a Workforce user forgets their device or their device is lost or stolen, they can authenticate using a backup device. The backup device available is defined by the information in your organization’s directory and can include a personal email address or alternative phone number.
Backup authentication is configured in the PingID admin portal. Learn more in Configuring backup authentication methods.