Creating an inbound provisioning rule (early access)
Create an inbound rule to define which users are provisioned to PingOne and how attributes are mapped between the external identity store and PingOne.
If you are creating a inbound rule for a connection through an LDAP gateway, refer to Creating an inbound provisioning rule for a connection through an LDAP gateway (early access).
Before you begin
Make sure you have created a connection.
|
Not all provisioning connection types support inbound provisioning. Learn more in Provisioning. You can add disabled connection to a source or target of a rule, but it must be enabled. Learn more in Connections. |
Steps
-
In the PingOne admin console, go to Integrations > Provisioning.
-
Click and then click New Rule.
-
For Sync Direction, select PingOne as Target.
-
For Available Connections, click next to the appropriate connection to set it as the source and then click Continue.
-
In the Rule Details panel, enter a Name and Description for the rule and then click Next.
-
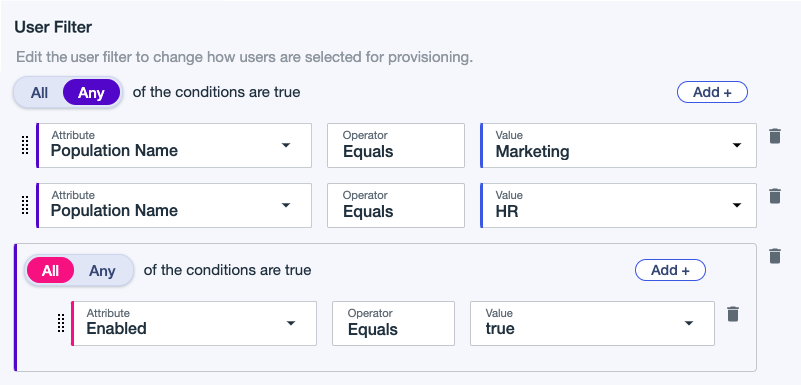
In the Directory Configuration panel, in the User Filter section, click Add Condition and define which users to include in provisioning based on population or user attributes. Learn more in Example user filters.
-
Enter the first condition:
-
Select All or Any to determine how the linked conditions will be evaluated: Boolean logical AND or OR.
-
Attribute: The user attribute to filter on.
-
Operator: Equals is the only operator supported at this time.
-
Value: Enter the appropriate value.
If you select a group in the filter, updating or deleting the group can cause the provisioning rule to resync.
If you select a group in the filter, the filter will include all users with any kind of membership in the group. Learn more in Groups.
-
-
(Optional) Click Add + to add another condition or condition set.
-
To delete a condition, click the Delete icon.
-
-
Click Next.
-
In the Attribute Mapping panel, map attributes between the source and PingOne to ensure users are provisioned correctly.
-
To add an attribute mapping, click Add and enter the source and target attributes.
-
To add a new source attribute, enter the attribute name. In the list, select the ADD: ADD:<attribute-name> attribute. Map the added attribute to a target attribute.
-
To use the expression builder, click the Gear icon. Learn more in Using the expression builder.
-
To delete a mapping, click the Delete icon.
Custom attributes created and mapped with the same name as an existing user sub attribute override the existing user sub attribute.
For example, if you create a custom attribute called country and the user sub attribute country already exists, the custom attribute overrides it even if you configure the attribute with a different letter case.
-
-
In the Onboarding Settings panel, define how users are matched, linked, and managed when onboarding into PingOne:
-
In the Populations list, select the population into which you want to sync users.
-
In Authoritative Identity Provider, PingOne is automatically set as the authoritative identity provider (IdP).
-
Select the Set default password for new users checkbox to specify the default password in PingOne for users synced in from an external identity store as a source.
-
Click Define Password Logic, to create a complex password using the functions in the expression builder. Learn more in Using the expression builder.
-
Select the Force password reset on first sign on checkbox to force users to reset their password the first time they authenticate through PingOne.
-
In the MFA Device Management list, select one of the following to control how the provisioner can impact MFA devices that are managed by a PingOne service (for example, PingOne MFA and PingID):
-
Merge with devices in PingOne (default): Select this option to add a device from the identity store into a user’s existing device in PingOne.
-
Overwrite devices in PingOne: Select this option to replace configured user devices in PingOne from the identity store. Only new devices mapped under attribute mappings are added.
-
Do not manage devices: Select this option to disable device management. This option is recommended for users using PingID in the same environment and to avoid unexpected device unpairing from nickname conflicts. Inbound provisioning and PingID use the same device nicknames and cause device unpairing.
-
-
-
Click Save.
-
To enable the rule, click the toggle at the top of the details panel to the right (blue).
You can disable the rule by clicking the toggle to the left (gray).
Result
The Sync Status appears and the rule is listed under Rules. Learn more about Sync status.
Example user filters early access
This section shows some example user filters to define users for provisioning.
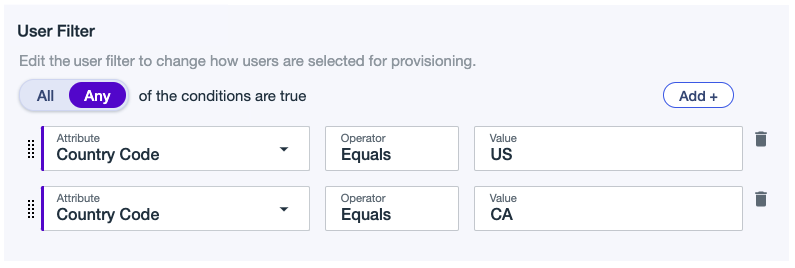
Example 1
A filter that includes users from the USA and Canada. Include users that match the following:
Country Code Equals US
OR
Country Code Equals CA
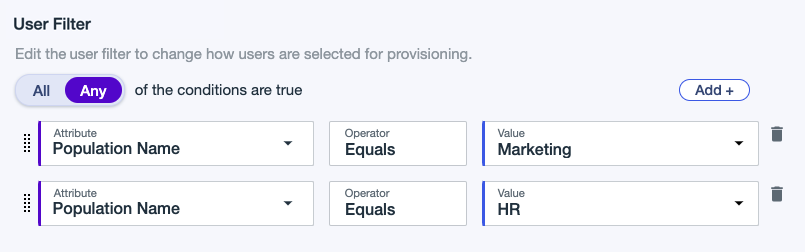
Example 2
A filter that includes users from the following populations:
Population Name Equals Marketing
OR
Population Name Equals HR
Authentication method management for inbound provisioning early access
Inbound provisioning manages all mapped email, voice, and SMS MFA attributes.
Nicknames
PingOne assigns nicknames to authentication methods (also called devices). The nicknames are used to identify authentication methods on user-facing pages, such as the Device Selection page.
Inbound provisioning uses nicknames when provisioning and synchronizing a user’s authentication methods. The following are the managed nicknames used by inbound provisioning:
-
SMS 1 -
SMS 2 -
SMS 3 -
Email 1 -
Email 2 -
Email 3 -
Voice 1 -
Voice 2 -
Voice 3
|
The inbound provisioner might unpair existing MFA devices if an existing device has a name that matches a managed nickname, as they’re assumed to be devices that the inbound provisioner should manage. In this case, where the managed nicknames are used by either PingID or manually entered, the recommended solution is to use the Do not manage. It is also possible to give your MFA device a different nickname as a workaround. |
Mapping attributes to nicknames
Each device nickname is associated with one attribute on the Attribute Mapping tab of the provisioning rule. For example, the Email
3 nickname holds the value of the MFA Device Email 3 attribute.
You can map these attributes on the Attribute Mapping tab of the provisioning rule.
Synchronization
When synchronizing a user’s authentication methods, inbound provisioning behaves as described in the following scenarios.
| Scenario | Action |
|---|---|
A device exists with a managed nickname, but the value does not match the value in the identity store. |
The provisioner deletes and recreates the device with the value from the identity store. |
A value matches between PingOne and the identity store, but the device uses an unmanaged nickname. |
The provisioner deletes and recreates the device with the appropriate managed nickname. |
A device exists with an unmanaged nickname and the value does not match the value in the identity store. |
The provisioner does not make any changes. |
Maximum number of authentication methods
Although inbound provisioning supports up to three SMS attributes, three email attributes, and three voice attributes, PingOne accepts a maximum of five authentication methods per user by default. You can adjust this in the Configuring MFA settings.