Setting up PingOne as the federated IdP for Microsoft Entra ID
As organizations expand their on-premise Active Directory (AD) infrastructure to the cloud with Microsoft Entra ID, you can configure PingOne as the federated identity provider (IdP) to fulfill two use cases:
- User authentication
-
-
When you set up PingOne as the federated IdP in Entra ID, users authenticate with PingOne when they attempt to use single sign-on (SSO) to access resources like Microsoft 365.
-
You can use Microsoft Entra Connect Sync to sync users from AD to Entra ID.
-
PingOne can authenticate users with the Kerberos or LDAP protocol.
-
- Hybrid join
-
-
Hybrid join simplifies device management and allows organizations to join devices to on-premise AD and the cloud with Entra ID.
-
You can use Entra Connect Sync to sync devices joined to the domain to Entra ID and make them eligible for hybrid join.
-
When you’re ready to start the hybrid join process to join a device to Entra ID, PingOne as the federated IdP enables the process by authenticating the device using the Kerberos protocol.
Device authentication using hybrid join is available as a limited access release for customers with a PingOne for Workforce Plus or Premium license in the North America region only and isn’t covered under standard Support service level agreements (SLAs). You can open support cases for feedback, bug reports, configuration questions, or other inquiries related, but resolution times for these cases will vary. These cases often require collaboration with our Engineering and Product teams, so response times might exceed the usual SLAs for your Support package.
Topics for this feature are draft documentation for limited access purposes only and aren’t complete or final.
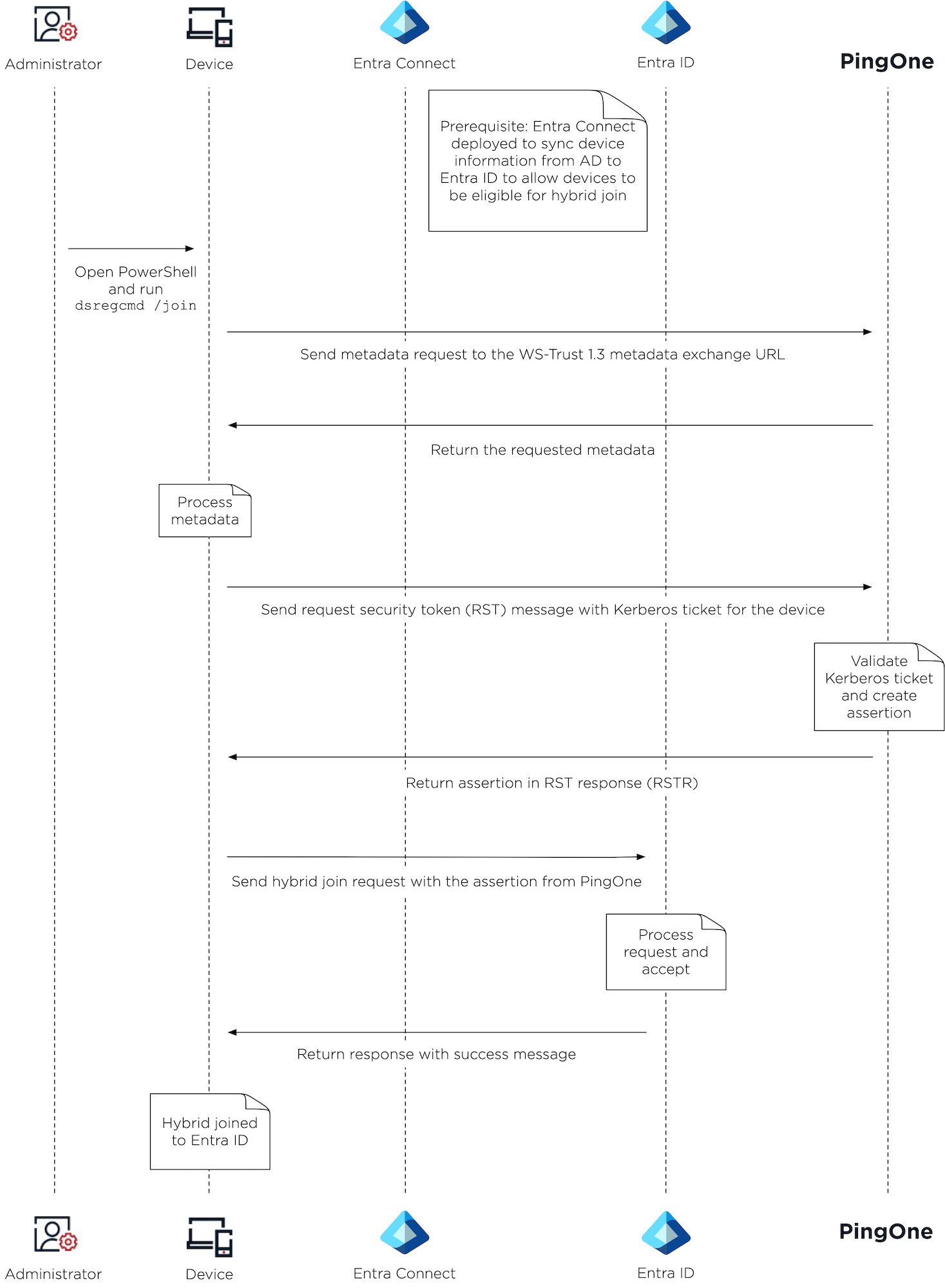
Hybrid join diagram
The following diagram shows the high-level process of setting up Entra hybrid join with PingOne as the federated IdP.
-
An administrator opens PowerShell and runs
dsregcmd /joinon the device. -
The device sends a metadata request to PingOne using the WS-Trust 1.3 metadata exchange URL.
-
PingOne returns the requested metadata to the device.
-
The device processes the metadata and sends a request security token (RST) message with a Kerberos ticket for the device to PingOne.
-
PingOne validates the Kerberos ticket, creates an assertion, and returns the assertion in an RST response (RSTR) to the device.
-
The device sends a hybrid join request with the assertion from PingOne to Entra ID.
-
Entra ID processes the request, accepts it if the configuration is set up properly, and returns a response with a success message.
-
The device is hybrid joined to Entra ID.
-
Goals
After completing this configuration, you’ll know how to:
-
Set up PingOne as the federated IdP for Entra ID.
-
Use Entra Connect Sync to sync users and devices from an AD domain to an Entra ID verified custom domain.
-
Enable users to authenticate with PingOne to access resources like Microsoft 365.
-
Enable hybrid join on your organization’s devices to sync them from AD to Entra ID.
What you’ll do
-
Complete the required prerequisites.
-
User authentication: Connect users to sign on to Microsoft 365 with PingOne as the federated IdP:
-
Hybrid join: Enable PingOne to process hybrid join requests from devices to sync devices from AD to Entra ID: