Reference and troubleshooting for Microsoft Entra hybrid join
Use this reference and troubleshooting information when setting up PingOne as the federated identity provider (IdP) with Microsoft Entra ID:
Reference
Use the information in this section to verify each attribute is mapped correctly when configuring PingOne as the federated identity provider (IdP) and enabling hybrid join.
Federated IdP settings
Verify the federated identity provider (IdP) settings in PingOne match the federated IdP settings in Microsoft Graph:
-
In the PingOne admin console, go to Applications > Applications and click the Microsoft 365 application.
You’ll compare the properties on the Overview tab with the settings in Microsoft Graph.
-
On a Windows-based computer, open PowerShell and select the Run as Administrator option.
-
Connect to Microsoft Graph and retrieve the current federated IdP settings using the following commands:
Connect to Microsoft Graph
Connect-MgGraph -Scopes "Directory.ReadWrite.All", "User.ReadWrite.All", "Domain.ReadWrite.All", "Directory.AccessAsUser.All" -NoWelcome
Retrieve current federated IdP settings
The following command uses an example custom domain of
imokatdi.ping-eng.com:Get-MgDomainFederationConfiguration -DomainId 'imokatdi.ping-eng.com' | Format-List
Sample output
ActiveSignInUri : https://sso.whosatwork.ca/wsf/sts/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e DisplayName : PingOne WS-Federation Identity Provider FederatedIdpMfaBehavior : acceptIfMfaDoneByFederatedIdp Id : 49d756d3-5c24-411f-b66c-fb8bc7625eaa IsSignedAuthenticationRequestRequired : IssuerUri : https://sso.whosatwork.ca/applications/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e MetadataExchangeUri : https://sso.whosatwork.ca/wsf/mex13/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e NextSigningCertificate : PassiveSignInUri : https://sso.whosatwork.ca/wsf/prp/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e PasswordResetUri : PreferredAuthenticationProtocol : wsFed PromptLoginBehavior : SignOutUri : https://sso.whosatwork.ca/wsf/prp/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e SigningCertificate : MII... SigningCertificateUpdateStatus : Microsoft.Graph.PowerShell.Models.MicrosoftGraphSigningCertificateUpdateStatus AdditionalProperties : {} -
Compare the results from Microsoft Graph with the properties on the Overview tab of the Microsoft 365 application in PingOne.
-
Verify the URL for
MetadataExchangeUriends with/wsf/mex13/<appId>, where<appId>is the application ID of the Microsoft 365 application in PingOne. -
If the URL ends with
/wsf/mex/<appId>(without13):-
Verify the Show WS-Trust 1.3 Metadata Exchange URL in Powershell cmdlets setting is enabled on the Configuration tab of the Microsoft 365 application in PingOne.
-
Follow the steps in Updating the federated IdP setting to update the
MetadataExchangeUriproperty.
-
-
Make sure to compare the other properties between PingOne and Microsoft Graph.
-
Attribute mappings for the Microsoft 365 application
If dsregcmd /join /debug fails with an error code of invalid_grant, error description of AADSTS51004, or both, verify the accounttype, onpremobjectguid, and primarysid attributes are configured with the required formats:
-
In the PingOne admin console, go to Applications > Applications and select the Microsoft 365 application.
-
On the Attribute Mappings tab, click the Pencil icon ().
-
For the
accounttypeattribute, click the More Options (⋮) icon and click Update NameFormat. -
In the Update NameFormat modal, verify the format matches the required format. If it doesn’t match, select the correct format in the list.
Refer to the table in Attribute mappings reference for the required format.
-
Repeat steps 3 and 4 for the
onpremobjectguidandprimarysidattributes. -
On the Attribute Mappings tab, click Save if you made any changes.
Attribute mappings reference
The following table lists the required attribute mappings for the Microsoft 365 application in PingOne:
Microsoft 365 application attribute mappings
| Attribute | Mapping |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
User type for cloud users
Refer to the attribute mappings in this section when you configure the LDAP gateway and add a user type for cloud users.
User link attributes
The following attributes must be mapped on the Lookup tab of the LDAP gateway in PingOne in the following order:
-
objectGUID -
objectSid -
dn -
sAMAccountName
Attribute mappings
The following table lists the required attribute mappings when you add a new user type to the LDAP gateway and click Use default values. The mappings can be added in any order.
LDAP gateway cloud user attribute mappings
| PingOne User Profile Attribute | LDAP Attribute |
|---|---|
Username |
|
Email Address |
|
Family Name |
|
Formatted |
|
Given Name |
|
Title |
|
Primary Phone |
|
Mobile Phone |
|
Street Address |
|
Locality |
|
Region |
|
Postal Code |
|
Country Code |
|
External ID |
|
The custom attribute you created to store |
|
|
The default source of External ID is the |
User type for hybrid joined devices
Refer to the attribute mappings in this section when you add a user type for hybrid joined devices to the LDAP gateway.
User link attributes
The following attributes must be added on the Lookup tab of the LDAP gateway in PingOne in the following order:
-
objectGUID -
objectSid -
dn -
sAMAccountName
Attribute mappings
The following table lists the attribute mappings when you:
-
Add a new user type to the LDAP gateway.
-
Click Use default values.
-
Delete all default values except those listed in the following table.
The mappings can be added in any order.
LDAP gateway hybrid joined devices attribute mappings
| PingOne User Profile Attribute | LDAP Attribute |
|---|---|
Username |
|
Nickname |
|
External ID |
|
The custom attribute you created to store |
|
|
The default source of External ID is the |
-
Use the same LDAP attribute for Username and External ID.
-
Map Nickname to
sAMAccountNameto represent device names and identify devices in PingOne. -
Create a custom attribute to map the required
objectSidattribute.Alternatively, you can map
objectSidto the system-provided Account ID. However, note that Account ID is typically associated with a user account.
Troubleshooting
Use the information in this section to troubleshoot the hybrid join process when running dsregcmd /join /debug in Validation.
dsregcmd /join /debug succeeded
When you run dsregcmd /join /debug, the following is an example response when the hybrid join process succeeds, and the device is successfully hybrid joined:
dsregcmd /join /debug succeeded example response
PS C:\Windows\System32> dsregcmd /join /debug
DsrCLI: logging initialized.
DsrCLI: logging initialized.
DsrCmdJoinHelper::Join: ClientRequestId: 7d05360e-378f-4e2e-81b1-0289d60b974bDsrCmdAccountMgr::IsDomainControllerAvailable: DsGetDcName success { domain:imokatdi.ping-eng.com forest:imokatdi.ping-eng.com domainController:\\IMOK-DC02.imokatdi.ping-eng.com isDcAvailable:true }
PreJoinChecks Complete.
preCheckResult: Join
deviceKeysHealthy: undefined
isJoined: undefined
isDcAvailable: YES
isSystem: YES
keyProvider: undefined
keyContainer: undefined
dsrInstance: undefined
elapsedSeconds: 0
resultCode: 0x0
Automatic device join pre-check tasks completed.
TenantInfo::Discover: Join Info { TenantType = Federated; AutoJoinEnabled = 1; TenandID = 07ec9af2-7ce5-4ab7-8638-115736bbf990; TenantName = imokatdi.ping-eng.com }
GetComputerTokenForADRS: Get token for ADRS
GetComputerTokenForADRS: Auth code URL: "https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/authorize"
GetComputerTokenForADRS: Token request authority: "https://login.microsoftonline.com/common"
AdalLog: Token is not available in the cache ; HRESULT: 0x0
AdalLog: Authority validation is enabled ; HRESULT: 0x0
AdalLog: Authority validation is completed ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken get refresh token info ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken- refresh token is not available ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken- returns false ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::UseWindowsIntegratedAuth w Tenant ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: AggregatedTokenRequest::UseWindowsIntegratedAuth- received realm info ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::GetAppliesTo: using resource ID "urn:federation:MicrosoftOnline" for authority "https://login.microsoftonline.com/common". ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: Webrequest opening connection ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: Webrequest has valid state ; HRESULT: 0x0
AdalLog: WebRequest Status:200 ; HRESULT: 0x0
AdalLog: Webrequest returns success for oauth response ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa9000f
AdalLog: HRESULT: 0x4aa9000d
Join request ID: 7d05360e-378f-4e2e-81b1-0289d60b974b
Join response time: Thu, 10 Jul 2025 17:22:14 GMT
Join HTTP status: 200
DsrCmdJoinHelper::Join: AutoEnrollAsComputer completed successfully
DSREGCMD_END_STATUS
AzureAdJoined : YES
EnterpriseJoined : NO
DeviceId : 3f0817b9-ca17-4714-ab81-f7b5943dec7b
Thumbprint : F243C1D15BF2CD9D33764913B003E9FB56543560
DeviceCertificateValidity : [ 2025-07-10 16:52:13.000 UTC -- 2035-07-10 17:22:13.000 UTC ]
KeyContainerId : 9b004996-ad3f-4d33-ba3c-c25bc5cbdb73
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
DeviceAuthStatus : SUCCESS
TenantName :
TenantId : 07ec9af2-7ce5-4ab7-8638-115736bbf990
AuthCodeUrl : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/authorize
AccessTokenUrl : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/token
MdmUrl :
MdmTouUrl :
MdmComplianceUrl :
SettingsUrl :
JoinSrvVersion : 2.0
JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/07ec9af2-7ce5-4ab7-8638-115736bbf990/
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/07ec9af2-7ce5-4ab7-8638-115736bbf990/
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net
Note the following in the response:
-
AzureAdJoined : YESmeans the hybrid join attempt succeeded, and the device is now hybrid joined to Entra ID. -
DeviceIdin the output matches the device ID of the device record in the Entra admin center. -
TenantIdis your Entra tenant ID.
dsregcmd /status after hybrid join
The following is an example response when you run dsregcmd /status after hybrid join succeeded:
dsregcmd /status example response
PS C:\Windows\System32> dsregcmd /status
+----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+
AzureAdJoined : YES
EnterpriseJoined : NO
DomainJoined : YES
DomainName : IMOKATDI
Device Name : IMOK-HYJD.imokatdi.ping-eng.com
+----------------------------------------------------------------------+
| Device Details |
+----------------------------------------------------------------------+
DeviceId : 3f0817b9-ca17-4714-ab81-f7b5943dec7b
Thumbprint : F243C1D15BF2CD9D33764913B003E9FB56543560
DeviceCertificateValidity : [ 2025-07-10 16:52:13.000 UTC -- 2035-07-10 17:22:13.000 UTC ]
KeyContainerId : 9b004996-ad3f-4d33-ba3c-c25bc5cbdb73
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
DeviceAuthStatus : SUCCESS
+----------------------------------------------------------------------+
| Tenant Details |
+----------------------------------------------------------------------+
TenantName :
TenantId : 07ec9af2-7ce5-4ab7-8638-115736bbf990
AuthCodeUrl : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/authorize
AccessTokenUrl : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/token
MdmUrl :
MdmTouUrl :
MdmComplianceUrl :
SettingsUrl :
JoinSrvVersion : 2.0
JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/07ec9af2-7ce5-4ab7-8638-115736bbf990/
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/07ec9af2-7ce5-4ab7-8638-115736bbf990/
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net
+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : NO
WorkplaceJoined : NO
WamDefaultSet : YES
WamDefaultAuthority : organizations
WamDefaultId : https://login.microsoft.com
WamDefaultGUID : {B16898C6-A148-4967-9171-64D755DA8520} (AzureAd)
+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : YES
AzureAdPrtUpdateTime : 2025-07-10 15:46:21.000 UTC
AzureAdPrtExpiryTime : 2025-07-24 15:46:20.000 UTC
AzureAdPrtAuthority : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990
EnterprisePrt : NO
EnterprisePrtAuthority :
+----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+
AadRecoveryEnabled : NO
Executing Account Name : IMOKATDI\ecotton, ecotton@imokatdi.ping-eng.com
KeySignTest : PASSED
+----------------------------------------------------------------------+
| IE Proxy Config for Current User |
+----------------------------------------------------------------------+
Auto Detect Settings : YES
Auto-Configuration URL :
Proxy Server List :
Proxy Bypass List :
+----------------------------------------------------------------------+
| WinHttp Default Proxy Config |
+----------------------------------------------------------------------+
Access Type : DIRECT
+----------------------------------------------------------------------+
| Ngc Prerequisite Check |
+----------------------------------------------------------------------+
IsDeviceJoined : YES
IsUserAzureAD : YES
PolicyEnabled : NO
PostLogonEnabled : YES
DeviceEligible : NO
SessionIsNotRemote : NO
CertEnrollment : none
PreReqResult : WillNotProvision
For more information, please visit https://www.microsoft.com/aadjerrors
Note the following in the response:
- In the
Device Statesection: -
-
DomainNameis your Active Directory (AD) domain name. -
Device Nameis the fully qualified name of the device.
-
- In the
SSO Statesection: -
-
AzureAdPrtindicates the device was issued a primary refresh token (PRT) for the signed-on user.
-
Learn more in Troubleshoot devices using the dsregcmd command in the Entra documentation.
dsregcmd /join /debug failed
Hybrid join can fail if the assertion from PingOne doesn’t contain the required attributes, values, or formats.
When you run dsregcmd /join /debug, the following is an example response if hybrid join fails because of PingOne and fallback sync:
dsregcmd /join /debug failed example response
PS C:\Windows\System32> dsregcmd /join /debug
DsrCLI: logging initialized.
DsrCLI: logging initialized.
DsrCmdJoinHelper::Join: ClientRequestId: 7b690c51-7ff3-4900-8875-18a409e1053eDsrCmdAccountMgr::IsDomainControllerAvailable: DsGetDcName success { domain:imokatdi.ping-eng.com forest:imokatdi.ping-eng.com domainController:\\IMOK-DC01.imokatdi.ping-eng.com isDcAvailable:true }
PreJoinChecks Complete.
preCheckResult: Join
deviceKeysHealthy: undefined
isJoined: undefined
isDcAvailable: YES
isSystem: YES
keyProvider: undefined
keyContainer: undefined
dsrInstance: undefined
elapsedSeconds: 0
resultCode: 0x0
Automatic device join pre-check tasks completed.
TenantInfo::Discover: Join Info { TenantType = Federated; AutoJoinEnabled = 1; TenandID = 07ec9af2-7ce5-4ab7-8638-115736bbf990; TenantName = imokatdi.ping-eng.com }
GetComputerTokenForADRS: Get token for ADRS
GetComputerTokenForADRS: Auth code URL: "https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/authorize"
GetComputerTokenForADRS: Token request authority: "https://login.microsoftonline.com/common"
AdalLog: Token is not available in the cache ; HRESULT: 0x0
AdalLog: Authority validation is enabled ; HRESULT: 0x0
AdalLog: Authority validation is completed ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken get refresh token info ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken- refresh token is not available ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken- returns false ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::UseWindowsIntegratedAuth w Tenant ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: AggregatedTokenRequest::UseWindowsIntegratedAuth- received realm info ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::GetAppliesTo: using resource ID "urn:federation:MicrosoftOnline" for authority "https://login.microsoftonline.com/common". ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: Webrequest opening connection ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: Webrequest has valid state ; HRESULT: 0x0
AdalLog: WebRequest Status:400 ; HRESULT: 0x0
AdalLog: Token response is not successfull. Status:400 ResponseText:{"error":"invalid_grant","error_description":"AADSTS51004: The user account {EUII Hidden} does not exist in the 07ec9af2-7ce5-4ab7-8638-115736bbf990 directory. To sign into this application, the account must be added to the directory. Trace ID: a441252e-1978-48b9-a07b-5926cfb74400 Correlation ID: 7b690c51-7ff3-4900-8875-18a409e1053e Timestamp: 2025-07-09 02:14:21Z","error_codes":[51004],"timestamp":"2025-07-09 02:14:21Z","trace_id":"a441252e-1978-48b9-a07b-5926cfb74400","correlation_id":"7b690c51-7ff3-4900-8875-18a409e1053e","error_uri":"https://login.microsoftonline.com/error?code=51004"} ; HRESULT: 0x0
AdalLog: Webrequest returns error code:invalid_grant and error description:AADSTS51004: The user account {EUII Hidden} does not exist in the 07ec9af2-7ce5-4ab7-8638-115736bbf990 directory. To sign into this application, the account must be added to the directory. Trace ID: a441252e-1978-48b9-a07b-5926cfb74400 Correlation ID: 7b690c51-7ff3-4900-8875-18a409e1053e Timestamp: 2025-07-09 02:14:21Z ; HRESULT: 0x0
AdalLog: HRESULT: 0xcaa20003
AdalLog: HRESULT: 0xcaa90006
GetStatus returned failure
AdalLog: HRESULT: 0xcaa1000e
GetComputerTokenForADRS: AdalErrorCode: 0xcaa1000e
AdalCorrelationId: 7b690c51-7ff3-4900-8875-18a409e1053e
AdalLog: HRESULT: 0xcaa1000e
GetStatus returned failure
AdalLog: HRESULT: 0xcaa90006
AdalLog: HRESULT: 0xcaa20003
AdalLog: Webrequest returns error code:invalid_grant and error description:AADSTS51004: The user account {EUII Hidden} does not exist in the 07ec9af2-7ce5-4ab7-8638-115736bbf990 directory. To sign into this application, the account must be added to the directory. Trace ID: a441252e-1978-48b9-a07b-5926cfb74400 Correlation ID: 7b690c51-7ff3-4900-8875-18a409e1053e Timestamp: 2025-07-09 02:14:21Z ; HRESULT: 0x0
AdalLog: Token response is not successfull. Status:400 ResponseText:{"error":"invalid_grant","error_description":"AADSTS51004: The user account {EUII Hidden} does not exist in the 07ec9af2-7ce5-4ab7-8638-115736bbf990 directory. To sign into this application, the account must be added to the directory. Trace ID: a441252e-1978-48b9-a07b-5926cfb74400 Correlation ID: 7b690c51-7ff3-4900-8875-18a409e1053e Timestamp: 2025-07-09 02:14:21Z","error_codes":[51004],"timestamp":"2025-07-09 02:14:21Z","trace_id":"a441252e-1978-48b9-a07b-5926cfb74400","correlation_id":"7b690c51-7ff3-4900-8875-18a409e1053e","error_uri":"https://login.microsoftonline.com/error?code=51004"} ; HRESULT: 0x0
AdalLog: WebRequest Status:400 ; HRESULT: 0x0
AdalLog: Webrequest has valid state ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: Webrequest opening connection ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: AggregatedTokenRequest::GetAppliesTo: using resource ID "urn:federation:MicrosoftOnline" for authority "https://login.microsoftonline.com/common". ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::UseWindowsIntegratedAuth- received realm info ; HRESULT: 0x0
AdalLog: HRESULT: 0x4aa90010
AdalLog: AggregatedTokenRequest::UseWindowsIntegratedAuth w Tenant ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken- returns false ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken- refresh token is not available ; HRESULT: 0x0
AdalLog: AggregatedTokenRequest::AcquireToken get refresh token info ; HRESULT: 0x0
AdalLog: Authority validation is completed ; HRESULT: 0x0
AdalLog: Authority validation is enabled ; HRESULT: 0x0
AdalLog: Token is not available in the cache ; HRESULT: 0x0
AutoEnrollAsComputer: Unable to retrieve access token. GetComputerTokenForADRS failed with error 0xcaa20003.
DsrCmdJoinHelper::Join: Federated ADRS join failed with error 0xcaa1000e. Try synchronized join.
Join request ID: 2b1b97b0-539e-4b48-91fe-55761b923b45
Join response time: Wed, 09 Jul 2025 02:14:22 GMT
Join HTTP status: 200
DsrCmdJoinHelper::Join: completed successfully
DSREGCMD_END_STATUS
AzureAdJoined : YES
EnterpriseJoined : NO
DeviceId : 3f0817b9-ca17-4714-ab81-f7b5943dec7b
Thumbprint : DADA1C38EBA6E6884F7DF92E22F057F689C07C8C
DeviceCertificateValidity : [ 2025-07-09 01:44:22.000 UTC -- 2035-07-09 02:14:22.000 UTC ]
KeyContainerId : 3fb81d8c-c49a-4ade-ac2b-8be7ebc4c54b
KeyProvider : Microsoft Software Key Storage Provider
TpmProtected : NO
DeviceAuthStatus : SUCCESS
TenantName :
TenantId : 07ec9af2-7ce5-4ab7-8638-115736bbf990
AuthCodeUrl : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/authorize
AccessTokenUrl : https://login.microsoftonline.com/07ec9af2-7ce5-4ab7-8638-115736bbf990/oauth2/token
MdmUrl :
MdmTouUrl :
MdmComplianceUrl :
SettingsUrl :
JoinSrvVersion : 2.0
JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/07ec9af2-7ce5-4ab7-8638-115736bbf990/
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/07ec9af2-7ce5-4ab7-8638-115736bbf990/
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net
Note the following errors in the response:
-
AdalLog: Webrequest returns error code:invalid_grant and error description:AADSTS51004 -
AutoEnrollAsComputer: Unable to retrieve access token GetComputerTokenForADRS failed with error 0xcaa20003 -
DsrCmdJoinHelper::Join: Federated ADRS join failed with error 0xcaa1000e
Attribute mappings issue
If you receive the previously noted errors when running dsregcmd /join /debug, verify the attributes and mappings are configured correctly in the user type for hybrid joined devices and Microsoft 365 application.
For the Microsoft 365 application, ensure each required attribute is configured with the correct attribute format.
Federation settings issue
Verify the federation settings of the verified custom domain using Microsoft Graph cmdlets.
In the following example, the verified custom domain is imokatdi.ping-eng.com, and the custom domain of the PingOne environment is sso.example.com:
PowerShell example with custom domain
PowerShell 7.5.2
PS C:\Windows\System32> Connect-MgGraph -Scopes "Directory.ReadWrite.All", "User.ReadWrite.All", "Domain.ReadWrite.All", "Directory.AccessAsUser.All" -NoWelcome
(Complete the sign on process as prompted by Microsoft.)
PS C:\Windows\System32> Get-MgDomainFederationConfiguration -DomainId "imokatdi.ping-eng.com" | Format-List
ActiveSignInUri : https://sso.example.com/wsf/sts/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e
DisplayName : PingOne WS-Federation Identity Provider
FederatedIdpMfaBehavior : acceptIfMfaDoneByFederatedIdp
Id : 49d756d3-5c24-411f-b66c-fb8bc7625eaa
IsSignedAuthenticationRequestRequired :
IssuerUri : https://sso.example.com/applications/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e
MetadataExchangeUri : https://sso.example.com/wsf/mex13/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e
NextSigningCertificate :
PassiveSignInUri : https://sso.example.com/wsf/prp/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e
PasswordResetUri :
PreferredAuthenticationProtocol : wsFed
PromptLoginBehavior :
SignOutUri : https://sso.example.com/wsf/prp/4afaa6b9-1497-44b6-b1ce-1a6d396f7f7e
SigningCertificate : MIIDATCCAemgAwIBAgIGAZXugDEBMA0GCSqGSIb3DQEBCwUAMDcxCzAJBgNVBAYTAkNBMRMwEQYDVQQKEwpEYW5ueSB0ZXN0MRMwEQYDVQQDEwpTaWdu
IE1lIFVwMB4XDTI1MDMzMTIzMTg1M1oXDTM1MDMyOTIzMTg1M1owNzELMAkGA1UEBhMCQ0ExEzARBgNVBAoTCkRhbm55IHRlc3QxEzARBgNVBAMTClNp
Z24gTWUgVXAwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC1oEADpq5sJ5ifgVtzt8rRBUYfLOMrvHowj05y2qB9wFdobvOsBqXq8mAPr+gz
Iq3MpTvYwsdLZ7yw55FNu59yTykVakAH+IKYfMe1X44IWvZQ4tmbvvtmmOlCsLDL8vPi6iJOyQHj1iUtDprb9YxeuQSRLJ4B98XGxQ5cJwurbbs3Zgfo
PrKTuoprmRlsxSllB0HVdGIh0WrBmfgJWmJXK0dOn4Rm0WtiU8P15aktBkI9Zn/pVEC8Ix6HAX6hkJT10GV9sMBXxQtGNB+OBT4OFTcomEAzLP2av6uU
6X60Mlv+79sTzFBnEDGZYWWMOTlEziVw3QJrbcm1OxTCSrklAgMBAAGjEzARMA8GA1UdEQQIMAaHBH8AAAEwDQYJKoZIhvcNAQELBQADggEBALUbyug+
xa99My7zqa1SHXY4F3sGCQPG7LZPWWGCd+6Plw/EXoGjnocx2Mg9WYCJCXTmchjXef7U4SDN5F8h3ZcaFAjVey9FjX2uvQt0v/l23+ZpQIVxulbIZKIE
a4iHrquSzDao3w8vIrL40ZvOUyvk+OjiP5PFOXlZ9kyN9EOfbuWjT1+sM49JmskVq70hfF4kO7o/+bmwMkE8rrKVocKjES/nGlcTit66FADkBDW1unCS
VWWRoNz4BuWa0M04tMj54aIqyZO3fXmje+l/xKUcpD3myfDhybncn0kIa0LmaqlNaCVm7zBjsyPi4NiYHAcJpzeeqMbC/1BV4Do0sYg=
SigningCertificateUpdateStatus : Microsoft.Graph.PowerShell.Models.MicrosoftGraphSigningCertificateUpdateStatus
AdditionalProperties : {}
Verify each setting against the Microsoft Graph PowerShell cmdlets on the Overview tab of the Microsoft 365 application in PingOne.
The MetadataExchangeUri value should contain /wsf/mex13/ in the path. If the path contains /wsf/mex/ without the 13, follow the steps in Updating the federated IdP setting to configure Entra ID to use the WS-Trust 1.3-compliant metadata exchange URL.
Fallback sync issue
If fallback sync isn’t disabled in Windows, the fallback mechanism initiates and succeeds with the following response from the previous example:
Try synchronized join DsrCmdJoinHelper::Join: completed successfully
We recommend disabling fallback sync when configuring PingOne to handle Entra hybrid join. Learn more in Troubleshoot devices using the dsregcmd command in the Entra documentation.
If you don’t disable fallback sync, failures will occur in other applications that use the security token service (STS) flow for authentication but don’t support the fallback mechanism.
Messages from Event Viewer
Depending on the device setup and the status of Entra Connect Sync, a device might try to hybrid join to Entra ID when it boots or when the user signs on. Log messages from failures and successful attempts can be found in the Windows Event Viewer application.
-
On a Windows-based computer, start Event Viewer.
-
Go to Applications and Service Logs > Microsoft > Windows > User Device Registration > Admin.
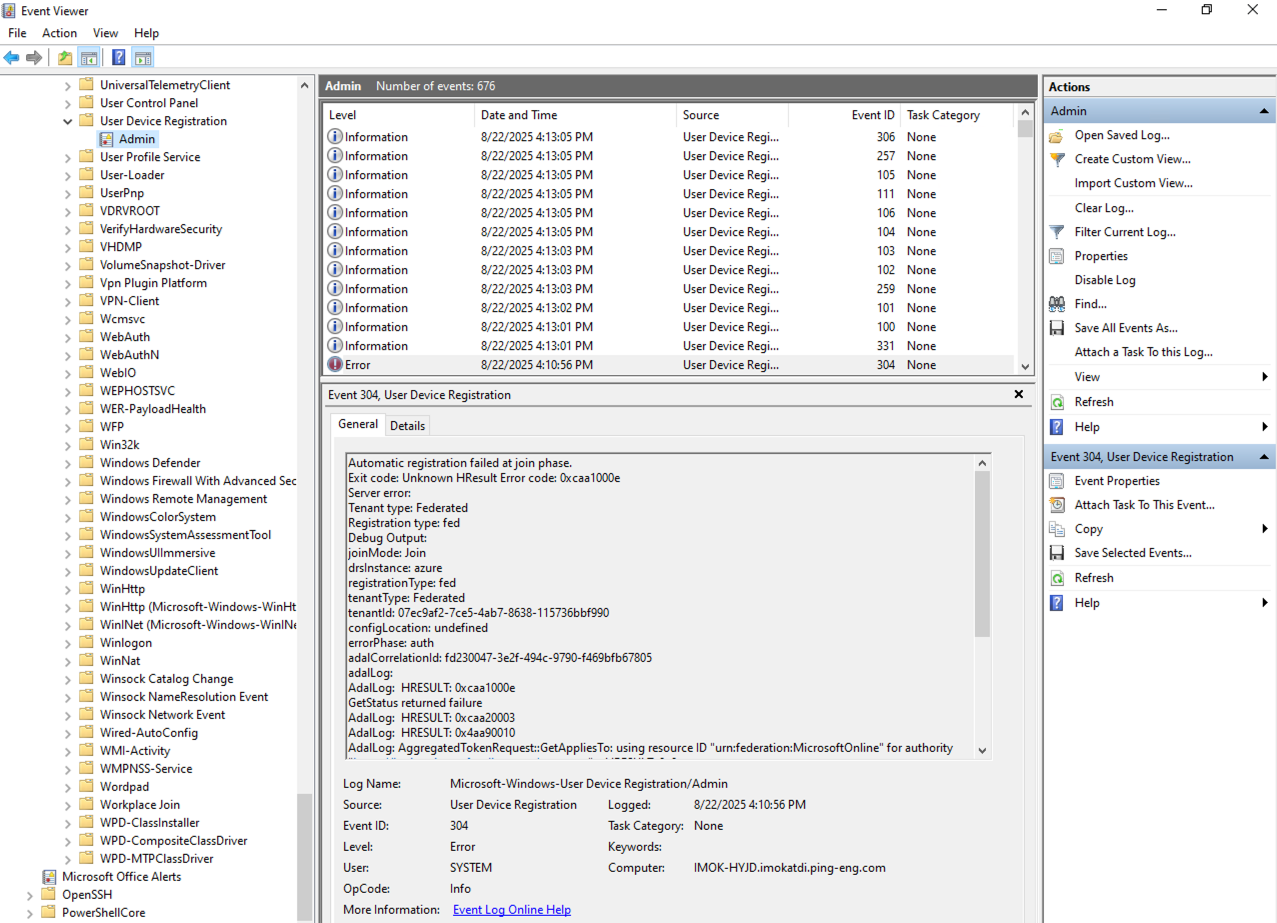
Log messages are displayed in the center panel and are similar to messages shown when you run the dsregcmd command.
Kerberos service account and AES encryption
The Kerberos service account must be configured to support Kerberos AES encryption.
-
On a Windows-based computer, open Active Directory Users and Computers and locate the service account you configured for the PingOne LDAP gateway Kerberos integration.
-
Right-click the service account and click Properties.
-
On the Account tab, in the Account Options section, select the This account supports Kerberos AES 256 bit encryption checkbox.
-
Restart the gateway instance.
Learn more in Starting a gateway instance.
-
Confirm that Kerberos authentication is working.
-
If Kerberos authentication still isn’t working, purge existing Kerberos tickets:
-
Open a command prompt and enter
klist purge. -
Sign off from Windows and sign back on.
-
Attempt Kerberos authentication.
-
-
If Kerberos authentication still isn’t working after purging existing Kerberos tickets, reset the password for the service account and purge existing Kerberos tickets again.